API Security: 1 Critical Bug Bounty Case Study on Swagger UI Vulnerability
By Satyam Pawale (@hackersatty)
About Me
API security
Hey security enthusiasts! I’m Satyam Pawale, better known in the cybersecurity and bug bounty community as @hackersatty. I specialize in identifying real-world security vulnerabilities in web applications using smart reconnaissance, API testing, and JavaScript analysis. I began my bug bounty journey in 2024 and have been passionate about securing web systems ever since.
In this blog post, I’ll walk you through a real vulnerability I discovered in a web application’s Swagger UI implementation—a bug that could have resulted in mass user account creation and unauthorized access. If you’re into security, bug bounty hunting, or want to learn how to identify misconfigurations in staging environments, you’re in the right place.
Introduction: Why API Security Matters
API is one of the most critical components of modern web application security. APIs expose sensitive backend logic and data to the front end—and if improperly secured, can lead to data leaks, broken authentication, or even total compromise.
One commonly overlooked entry point in APIs is the Swagger UI, an auto-generated documentation and testing interface for RESTful APIs. While incredibly useful for developers, exposing it publicly without proper access controls can be a severe vulnerability.
In this article, I’ll show how I discovered a broken authentication vulnerability via Swagger UI in a staging environment, how I exploited it, what the impact was, and how to prevent similar issues.
The Vulnerability Discovery
While testing a private bug bounty program, I decided to focus on their staging environment—specifically the staging-api.example.com domain. Staging environments often mirror production and, if misconfigured, can expose sensitive endpoints without authentication.
I opened the following Swagger URL:
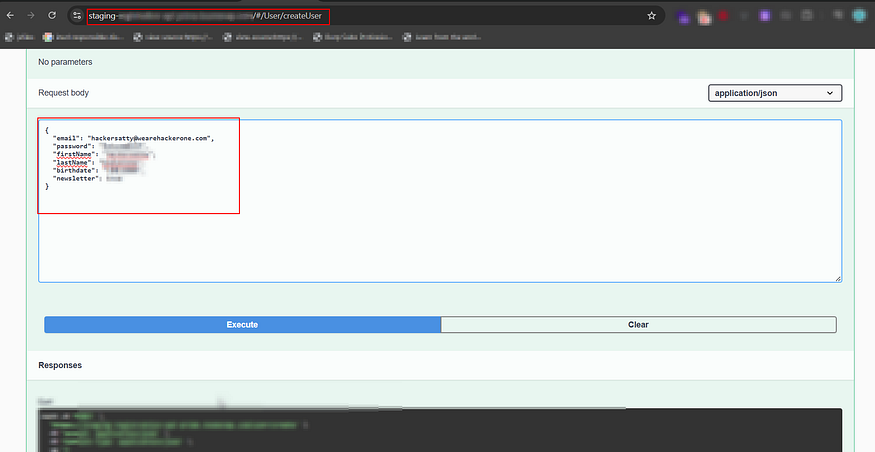
https://staging-api.example.com/#/User/createUserTo my surprise, no authentication was required to access the API documentation. I explored the /User/createUser, /resetPassword, and /createApplication endpoints—and all of them were completely open.
This misconfiguration meant any attacker could:
-
Create new user accounts without restriction
-
Reset passwords of real users
-
Abuse business logic and backend APIs
Step-by-Step Breakdown
1. Swagger UI Access
Visiting the staging Swagger endpoint gave me access to full documentation, including methods, request formats, and example payloads.
2. Crafting a POST Request
Using the built-in testing tools in Swagger UI, I submitted the following payload to create a user account:
{
"email": "user@example.com",
"password": "Test@123",
"firstName": "Example",
"lastName": "User",
"birthdate": "2000-01-01",
"newsletter": true
}3. Success Without Authentication
A 200 OK response confirmed the user was successfully created—even though I wasn’t logged in or providing any kind of token. This confirmed the vulnerability.
🔒 Pro tip: Always investigate /swagger, /api, or /docs routes in staging and development environments. These can reveal sensitive APIs.
Proof of Concept
The vulnerability was demonstrated entirely through Swagger UI. No tools like Burp Suite or Postman were initially required. Later, I used Burp Suite for advanced validation and to inspect tokens, headers, and replay scenarios.
This reinforces the point that many critical vulnerabilities can be uncovered with just your browser and some curiosity.
Security Impact
The security implications of this issue were serious:
1. Mass Account Creation
An attacker could flood the system with fake accounts, overwhelming resources or hiding among legitimate users.
Endpoints like resetPassword or createApplication could be abused for privilege escalation or service disruption.
3. Production Exposure
If staging APIs use shared infrastructure or connect to production systems, this kind of issue can quickly escalate.
🔗 Related Internal Link:
How I Leaked Admin Metadata via Token Swap in a Real Bug Bounty
Link to OWASP page for vulnerabilities:
Root Cause: Broken Authentication in API Security
This is a textbook example of Broken Authentication, listed as one of the top vulnerabilities in the OWASP Security Top 10. Specifically:
-
API2: Broken User Authentication — No session token, API key, or OAuth token was required.
-
API3: Excessive Data Exposure — Full endpoint functionality was exposed via Swagger.
Remediation Recommendations
I recommended the following to the program:
Add Authentication
Use OAuth 2.0, session tokens, or API keys to authenticate every sensitive endpoint—even in staging.
Restrict Swagger UI Access
Limit access using IP whitelisting, HTTP Basic Auth, or restrict it behind an internal network or VPN.
Conduct Regular Security Audits
Use tools like OWASP ZAP, Burp Suite, or Postman Security Collections to validate access control and input sanitization.
🔗 External Link: OWASP API Security Top 10
Want to explore more real-world bug bounty techniques? Check Out My Other Bug Bounty Blogs
Key Takeaways for Bug Bounty Hunters
-
Don’t ignore staging — They often mirror production but lack protections.
-
Swagger UI is a double-edged sword — Great for developers, dangerous for public exposure.
-
Manual recon is powerful — Combine tools with smart observation.
-
Use automation wisely — Tools like Nuclei, Subfinder, or Kiterunner help, but don’t replace manual logic.
🔗 Internal Link: The Ultimate IDOR Bug Bounty Methodology (2025 Guide)
Final Thoughts: Keep Hunting, Keep Learning
This was one of my earliest critical bug bounty finds and taught me that APIs are one of the most vulnerable attack surfaces today. With tools like Swagger, Postman, and Burp Suite at your disposal, you don’t need to brute force—just observe and test logically.
🔍 API is more than headers and tokens—it’s about understanding how developers structure access and how attackers think.
If you found this write-up helpful, feel free to connect with me on LinkedIn or follow my work on Twitter.
Until next time, stay curious and stay secure! 🔐

One thought on “API Security: 1 Critical Bug Bounty Case Study on Swagger UI Vulnerability”