5 Effective Bug Bounty Tips to Detect Unauthorized Access to Admin Pages
By Satyam Pawale (@hackersatty)
About Me
Hi everyone! I’m Satyam Pawale, also known as @hackersatty in the bug bounty community. Since 2024, I’ve been passionate about identifying and reporting security vulnerabilities to help make the web safer for everyone.
Introduction
Unauthorized Access to Admin Pages is one of the most critical vulnerabilities that arise from security oversights in today’s digital landscape. This article explores how I discovered unauthorized access to admin pages via vulnerable API endpoints on a target subdomain. It highlights the associated risks, exploitation methods, and actionable remediation steps to help developers secure their systems against such threats.
Discovery Process
While conducting routine reconnaissance on a target domain (anonymized for security), I paid special attention to its subdomains — often overlooked but full of valuable information for attackers and researchers alike.
-
Subdomain Enumeration:
Using tools like Subfinder and HTTPX, I identified multiple subdomains. One particular subdomain showed unexpected responses worth further investigation. -
Directory Enumeration:
By running directory brute force and endpoint discovery, I found several administrative endpoints without authentication:
-
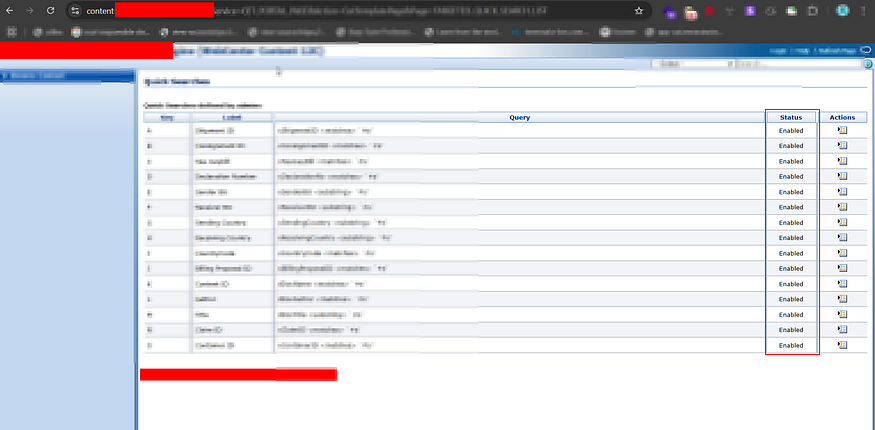
/TARGETED_QUICK_SEARCH_LIST -
/SCHEMA_BROWSE_POPUP -
/STANDARD_QUERY_PAGE
These endpoints were vulnerable to unauthorized access and exposed sensitive backend data.
Vulnerable Endpoints and Risks
1. /TARGETED_QUICK_SEARCH_LIST
Risk: This endpoint exposes template pages and sensitive metadata that could help attackers understand the internal structure of the system.
2. /SCHEMA_BROWSE_POPUP
Risk: Allows manipulation of query parameters such as whereClause, potentially enabling unauthorized database schema access or data insertion.
3. /STANDARD_QUERY_PAGE
Risk: Query parameters can be tampered with to retrieve confidential internal data.
All these endpoints lacked proper authentication and authorization, making them prime targets for exploitation.
Exploitation Steps
-
Accessing the Endpoints:
Navigating directly to the above endpoints, I confirmed that no authentication prompt was required. -
Parameter Manipulation:
I tested parameters likefieldName,whereClause, andSearchQueryFormatto explore unauthorized data access. For example:
-
Inspecting Responses:
Responses contained exposed metadata, detailed database schema information, and sensitive data, confirming the lack of access controls.
Impact Assessment
The consequences of such vulnerabilities are severe:
-
Confidentiality Breach: Unauthorized users gain access to internal metadata and system details.
-
Data Integrity Risks: Attackers could manipulate data, corrupting the platform’s reliability.
-
Access Control Bypass: Attackers can perform admin-level actions without permission.
These issues are classic examples of Broken Access Control, a top concern in the OWASP Top 10 vulnerabilities.
Suggested additions:
- Link to OWASP page for vulnerabilities:
- Owasp
Recommendations for Remediation
-
Implement Proper Authentication and Authorization:
Ensure all sensitive endpoints require authentication and enforce role-based access control (RBAC) to restrict access strictly. -
Secure API Endpoints:
Use API gateways, implement OAuth 2.0 or similar standards for authorization, and validate all input parameters rigorously. -
Regular Security Audits:
Conduct periodic security reviews and code audits to detect and fix vulnerabilities proactively. -
Monitor and Log Access:
Maintain comprehensive logs and set up monitoring for unauthorized access attempts to respond quickly.
Key Takeaways
-
Always protect administrative endpoints with strong authentication and authorization.
-
Regular audits and monitoring are essential to detect security gaps.
-
Stay updated on common risks like Broken Access Control and follow best security practices.
Further Reading
Final Thoughts
Discovering and responsibly reporting vulnerabilities in admin endpoints requires attention to detail and ethical commitment. This case study highlights how overlooked subdomains and endpoints can pose significant security risks.
By sharing these findings, I aim to encourage developers and organizations to prioritize robust security measures and help foster a safer digital environment.
If you found this article helpful or have any feedback, feel free to connect with me on LinkedIn or follow me on Twitter. Let’s continue growing together in cybersecurity!
