GraphQL Introspection Exposure: The 1 Hidden Blueprint That Could Undermine Your Entire Backend
About Me
I’m Satyam Pawale, better known in the bug bounty world as @hackersatty. As a dedicated security researcher, I specialize in uncovering complex misconfigurations and information disclosures—especially in web servers and directory services.
My toolkit includes Shodan, Burp Suite, custom scripts, and creative reconnaissance techniques.
In this article, I’ll guide you through the discovery and exploitation of a GraphQL introspection exposure vulnerability—so you can sharpen your bug bounty skills and better secure GraphQL-based APIs in production environments.
Introduction
Graphql introspection exposure is revolutionizing API design by allowing clients to request exactly what they need and nothing more. But with great flexibility comes great responsibility.
One of the most overlooked yet dangerous misconfigurations in GraphQL is leaving introspection enabled in production environments.
If attackers can query your schema structure without any authentication, they’re holding a blueprint of your backend, including sensitive endpoints, user object fields, and internal logic.
This post dives deep into how I discovered such an exposure on hackersattybugs.online/graphql, what I found inside, and how you can protect your APIs.
What is GraphQL Introspection?
GraphQL introspection is a self-documenting feature that allows developers and clients to ask a GraphQL server about its schema.
Common introspection queries can return:
-
All types and their fields
-
Available queries and mutations
-
Nested relationships and object structures
-
Custom directives and authentication mechanisms
This is great for development and tools like GraphiQL or Apollo Studio—but in production, it becomes a critical information disclosure vulnerability.
Why Introspection Shouldn’t Be Public
According to OWASP, unauthenticated introspection is equivalent to handing over your entire backend map to an attacker.
Even without credentials, attackers can:
-
Enumerate all API functionality
-
Identify sensitive objects (like
User,Token,AdminPanel) -
Prepare precise injection or manipulation attacks
-
Target misconfigured or undocumented endpoints
In many cases, introspection is the first step toward chaining bigger GraphQL exploits like:
-
Bypassing authorization
-
Performing privilege escalation
-
Triggering denial of service with complex nested queries
Discovery on hackersattybugs.online
While manually reviewing assets under the target scope, I came across a public configuration file that listed internal services and base URLs. One of them pointed to:
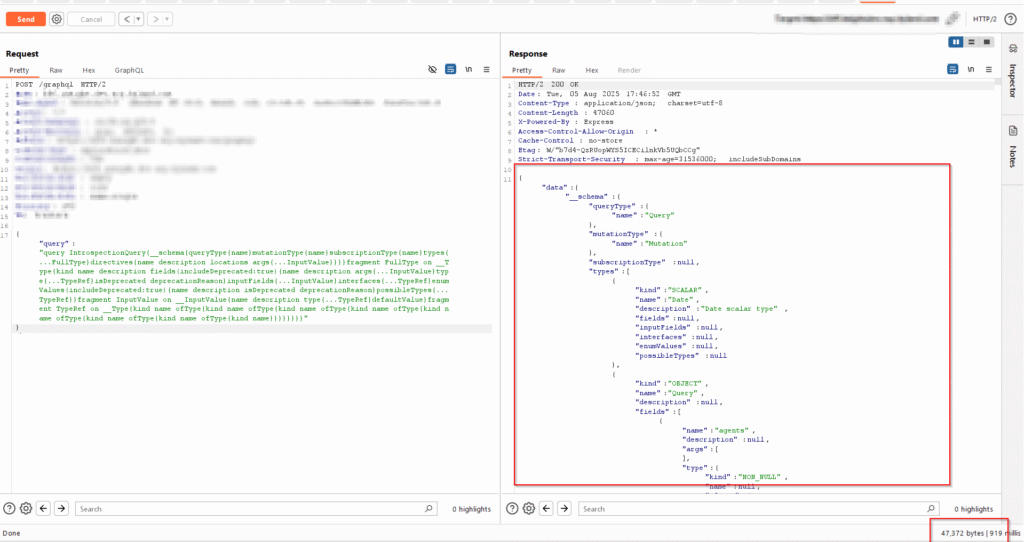
I loaded this endpoint in Postman and tried a basic introspection query without any authentication token.
To my surprise—it responded with the entire schema.
That’s when I knew this was a serious issue.
Step-by-Step Exploitation
Here’s how I confirmed the introspection exposure and explored the schema:
Step 1: Basic Schema Query
Response: A complete dump of all types, objects, and fields used in the backend.
Step 2: Discover Sensitive Types
I looked for common sensitive types like:
-
User -
Session -
AdminConfig -
AccessToken -
FileMetadata
And yes, I found all of them — completely unauthenticated.
Step 3: Explore Available Queries
Using this payload:
I mapped every available graphql introspection exposure to clients.
Step 4: Look for Mutations
Then I checked mutations, which can be more dangerous since they change data:
Some interesting ones I discovered:
-
resetPassword -
updateUser -
createInternalToken -
uploadFile -
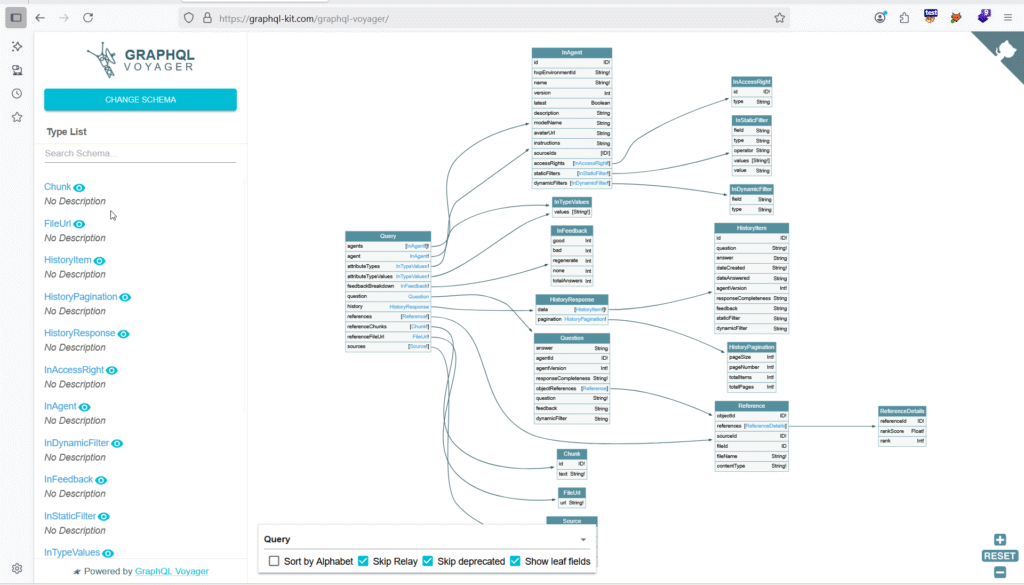
GraphQL introspection endpoint leaking backend schema in a real bug bounty case.
None of these required authentication to view.
Proof of Concept Payload
Here’s a final POC payload that anyone could run without a token:
Insert Screenshot Here
Alt text: GraphQL introspection query showing full schema exposure on hackersattybugs.online
What I Found Inside
Through this exposed schema, I was able to:
-
Discover all internal query names
-
Find user objects with fields like
email,passwordHash,role, andlastLogin -
Identify undocumented internal APIs for administrative operations
-
Learn about file metadata storage, possibly tied to S3 buckets or internal storage
-
Confirm that no authorization checks were triggered during introspection
Real-World Risks of Introspection Exposure
Leaving introspection open is like publishing your backend’s API docs to the entire internet.
Attackers can:
-
Reverse-engineer business logic
-
Target sensitive fields for injection or manipulation
-
Combine with SSRF or IDOR for deeper exploits
-
Abuse undocumented functionality for account takeover
Case Study:
PortSwigger’s GraphQL Academy shows how introspection can lead to unauthorized access to user data by revealing the structure of user-related queries.
How to Disable Introspection
Here’s how to disable introspection in your production GraphQL APIs, depending on the tech stack:
Apollo Server (Node.js)
GraphQL-Java (Spring Boot)
Express-GraphQL
Best Practices for Securing GraphQL APIs
To avoid introspection exposure and related attacks:
✅ Disable introspection in production
✅ Use depth and complexity limiting (e.g., graphql-depth-limit)
✅ Require authentication for all GraphQL endpoints
✅ Rate limit introspection queries
✅ Log and monitor query patterns for anomalies
✅ Avoid exposing sensitive fields in user objects (e.g., password, token)
Also, tools like LokiJS, GraphQL Armor, and Shield can add query-level protections to your stack.
Conclusion
graphql introspection exposure is an amazing tool for developers—but a dangerous threat in the hands of an attacker when left exposed.
In this case, I found an unauthenticated GraphQL endpoint that leaked the full schema and revealed sensitive internal operations.
The fix was simple: disable introspection in production.
If you’re running a bug bounty program or building secure APIs, this should be a mandatory checklist item.
Final Thoughts: Other Bug Bounty Blogs
GraphQL introspection exposure is just one example of how visibility can become a vulnerability.
With the right mindset and tools, bug bounty hunters can uncover massive flaws—without even needing authentication.
Remember: always stay within scope, validate what you find, and follow responsible disclosure guidelines.
Keep exploring. Keep hunting.
👉 Read more: How I Found Critical IDOR on Another Site
