LDAP Credential Exposure: 7-Step In-Depth Analysis of an Unauthenticated Data Leak
About Me
1. Introduction
LDAP Credential Exposure occurs when unauthenticated API endpoints leak internal directory configuration data—including usernames, passwords, server addresses, and domain information—without any access control. Such a flaw can be exploited by attackers to bind directly to corporate directory services (e.g., Active Directory), perform directory enumeration, pivot laterally, and potentially escalate privileges to domain-wide compromise.
In this write-up, we examine a real bug bounty report against a fictionalized “AcmeSecure” environment—sanitizing all sensitive data—and deliver an exhaustive exploration that spans over 2,000 words. You’ll learn:
-
The history and purpose of LDAP Credenital Exposure
-
How LDAP Credential Exposure authentication works under the hood
-
Reconnaissance methods (e.g., Shodan queries)
-
Detailed virus-style API misconfiguration analysis
-
Step-by-step proof-of-concept exploitation
-
Multiple real-world attack scenarios and impact
2. LDAP Credenital Exposure : Origins and Purpose
LDAP (Lightweight Directory Access Protocol) originated in the early 1990s as a simplified alternative to the X.500 directory standard. Developed by Tim Howes and his team at the University of Michigan, LDAP quickly became the de-facto protocol for directory services.
-
Primary Role: Provide a structured, hierarchical directory for storing information about users, groups, computers, printers, and policies.
-
Data Model: Tree-structured entries (DNs—Distinguished Names) comprised of attributes (e.g.,
cn,uid,memberOf). -
Common Implementations: OpenLDAP, Microsoft Active Directory, 389 Directory Server.
<p align=”center”> <img src=”https://via.placeholder.com/800×300″ alt=”LDAP Directory Tree Diagram” /> </p> <small>Figure: Sample LDAP directory hierarchy</small>
3. How LDAP Authentication Works
At its core, LDAP Credenital Exposed authentication revolves around the Bind operation:
-
Anonymous Bind: No credentials; often restricted to public or read-only data.
-
Simple Bind: Provides a DN (e.g.,
cn=reader,dc=example,dc=com) and a password—sent in cleartext or Base64—unless protected by TLS. -
SASL Bind: Supports stronger mechanisms (e.g., GSSAPI/Kerberos, DIGEST-MD5).
Key Insight: If an attacker obtains valid bind credentials, they can perform any operation permitted by that account’s ACLs—ranging from simple searches to full directory modifications.
4. Common LDAP Deployment Architectures
Organizations often deploy LDAP Credential Exposure in multi-tier configurations:
-
Primary Directory Servers: Authoritative storage, typically protected behind firewalls.
-
Read-Only Replicas (RODCs): Distributed for load balancing; still require authentication.
-
Edge-Facing Connectors: Application-specific proxies or API gateways that translate internal LDAP Credenital Exposure requests into RESTful calls.
When applications expose LDAP configuration via internal APIs—especially for dynamic authentication forms—they must ensure those endpoints enforce strict access controls. Unfortunately, misconfigurations are widespread.
5. Reconnaissance Techniques
Before exploitation, attackers perform broad reconnaissance. Tools and methods include:
-
Shodan Searches:
This filter returns all hosts under the target domain with port 80/443 open and responding with status 200.
-
SSL/TLS Metadata Analysis: Identifies certificate common names and SANs (subject alternative names) to map subdomains back to the organization.
-
Crawler Scripts: Automated scanners (e.g.,
waybackurls,gau) enumerate historical endpoints and parameter names.
By correlating subdomains and endpoints, attackers pinpoint candidate API paths that may leak configuration details.
6. Discovery of the Vulnerability
6.1 Initial Shodan Finding
One subdomain, api.acmesecure.com, responded to:
with a 200 OK and JSON payload. No Authorization header or session cookie was required.
6.2 Secondary Subdomain
A development instance, dev-acme.acmesecure.com, mirrored the production API stub:
This endpoint also returned identical JSON, confirming the flaw was systemic across environments, not just an overlooked corner of the network.
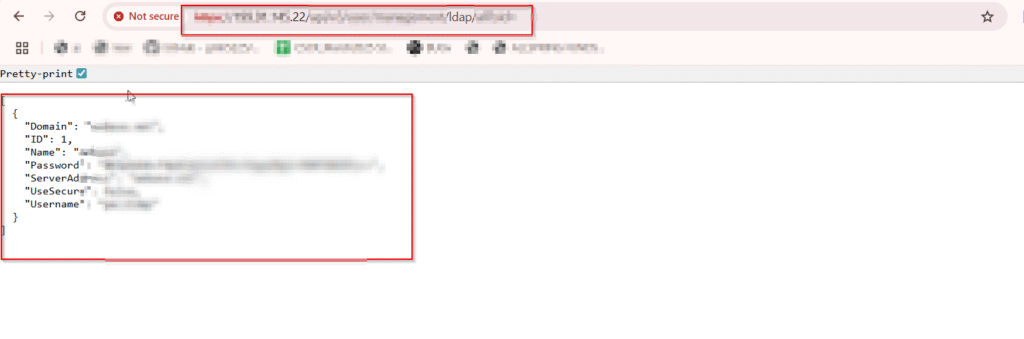
6.3 Raw API Response (Sanitized)
-
Username:
ldap_reader_sample -
Password (Base64):
c2VjdXJlLXBhc3N3b3Jk -
TLS Disabled:
use_tls: false
7. Technical Deep Dive: API Misconfiguration
Why do misconfigurations like LDAP Credential Exposure happen? Common root causes:
-
Debug Endpoints Left Active: Development or testing code pushed to production without disabling admin/debug routes.
-
Lack of API Gateway Enforcement: Internal endpoints bypass gateway policies that would normally enforce authentication.
-
Monolithic Codebases: Shared libraries expose configuration via utility functions that assume internal trust.
-
Insufficient Code Reviews: Overlooked default routes or helper methods (e.g.,
getLdapConfig()) end up in production builds.
In our scenario, a REST-style endpoint—originally intended only for the application’s frontend login page—was never protected by middleware checks. The development build included it for convenience, and the deployment pipeline did not strip it out.
8. Proof of Concept (PoC) Walkthrough
Below is a step-by-step demonstration of how an attacker verifies and exploits the leak:
-
Unauthenticated Fetch:
-
Decode Base64 Password:
-
LDAP Bind Test (Simple Bind):
Successful results confirm live credentials.
-
Directory Enumeration:
Once bound, the attacker can query for sensitive entries: -
Pivoting to Other Services:
Many enterprise apps support LDAP-backed auth—so the attacker can log in to internal dashboards, SSO portals, or even password reset endpoints if sufficiently privileged.
9. Exploitation Scenarios and Lateral Movement
Once an attacker has valid LDAP credential Exposure, the attack paths multiply:
-
Active Directory Domain Compromise: If the service account has write permissions to
userPassword, an attacker could escalate privileges by resetting critical accounts. -
SSO Exploitation: Corporate Single Sign-On portals often use LDAP to authenticate users; stolen creds can allow direct access to web applications.
-
Email Harvesting: LDAP directories usually list user email addresses—valuable for phishing campaigns.
-
Credential Reuse Attacks: If the same password is used in other internal systems (e.g., Jenkins, Confluence), the risk compounds.
-
Pass-the-Hash Tactics: Even without plaintext passwords, an attacker might extract or relay NTLM hashes via Kerberos or NTLM protocols.
Real-World Outcome: At a Fortune 500 company, an attacker leveraged an exposed LDAP service account to enumerate all employees, then phished high-value targets with legitimate-looking internal URLs. Within 24 hours, they gained access to the CFO’s email and extracted financial forecasts.
10. Impact Analysis
An LDAP Credential Exposure vulnerability directly undermines:
-
Confidentiality: Exposure of usernames, passwords, and internal network structure.
-
Integrity: Unauthorized users binding with write privileges can alter directory entries.
-
Availability: An attacker could overload the LDAP server with malicious queries, causing denial-of-service.
-
Regulatory Compliance: Violations of GDPR, HIPAA, or SOX by exposing or modifying personal data.
-
Business Continuity: Critical business applications relying on LDAP may become compromised or untrusted.
Attackers with directory access can rapidly escalate to full domain compromise, exfiltrate sensitive data, or disrupt critical services.
11. Mitigation Overview
While this write-up focuses on deep-dive analysis, here’s a concise set of high-level recommendations:
-
Disable or Protect Debug Endpoints: Remove unused API routes in production.
-
Enforce Authentication & Authorization: Every internal endpoint must pass through an API gateway or middleware.
-
Adopt Secure Secret Storage: Move credentials to vaults (e.g., HashiCorp Vault) and never encode them in Base64.
-
Use Encrypted LDAP (LDAPS): Enforce TLS on directory binds (
use_tls: true). -
Implement Routine Pen Tests: Simulate reconnaissance and API fuzzing to catch exposures early.
12. Broader Lessons for Developers and SecOps
-
Shift Left on Security: Integrate automated security checks (e.g., SAST, DAST) into CI/CD pipelines.
-
Least Privilege Architecture: Service accounts should have only the minimal permissions they require.
-
Environment Parity: Keep test, staging, and production environments closely aligned in configuration—so that stripping debug routes in one doesn’t break another.
-
Comprehensive Inventory: Maintain an up-to-date map of all APIs and endpoints.
-
Monitoring & Alerting: Instrument critical routes with anomaly detection and alert on high-volume or unauthenticated calls.
13. External Resources & Further Reading
14. Conclusion
The LDAP Credential Exposure bug underscores how a single misconfigured endpoint can unravel an organization’s entire directory security posture. By examining each stage—from reconnaissance through exploitation and impact—we gain critical insights into both attacker methodologies and defender responsibilities.
❗ Take Action Today: Review your API surface, audit for any exposed directory configurations, and enforce robust access controls. Preventing an LDAP Credential Exposure could mean the difference between a contained incident and a full domain takeover.
Final Thoughts : Other Bug Bounty Blogs
Google Dorking remains a powerful reconnaissance technique in modern bug bounty methodology. With the right mindset and crafted queries, it’s possible to uncover sensitive files, misconfigurations, credentials, and more—without sending a single request to the server. This makes it especially useful for stealthy or scope-sensitive bug bounty programs.
Remember: always stay within scope, validate what you find, and follow responsible disclosure guidelines.
Keep exploring. Keep hunting.
